Emerging challenges in Organized Cyber-Crime and Terrorist Networks
Discovering the challenges and available solutions against organized cyber-crime and terrorist network for building secure societies of the future
Organized Crime (OC) and Terrorist Networks (TN) have risen to major and persistent threats for the European Union and its population. The IT growth of the past decade caused a migration of OC/TN to the cyber domain as well as the introduction of cybercrime. As a consequence, the technological dimensions of criminal activities are becoming more relevant and challenges ranging from the identification of criminal activities up to the understanding of engagement processes, are even more complicated. In this context, this article aims to highlight the major challenges in in the European community by distinguishing between basic issues and advanced issues that are emerging due to the Internet.
The modern society is surrounded by systems and services that are mostly build in terms of physical, mechanical, and electrical systems which in turn are closely linked and controlled by ICT infrastructures. Even the media, which are massively used for advertising purposes, have radically evolved and become more dynamic and interactive. On one hand, this brings benefits in terms of the well-being of life through the use of more effective services ranging from sending messages, transferring money, tele-medicine and so on, worldwide in real time. On the other hand, if used maliciously they can represent a great threat to humanity. In fact, through their improper use, it is possible to (i) launch attacks and compromise at far distance industries, factories, systems and so on (ii) threaten people; (iii) advertise illegal activities, sell drug via dark markets, etc. Due to the high degree of activity distribution at the individual level, which is enabled by such technologies, the fighting process is getting more difficult. Consequently, it is necessary to identify what the main problems are, and get increased awareness regarding the functioning of such criminal systems.
As a consequence, an important discriminating element, considered in this analysis, is the IT part, which has led to the identification of two main categories of issues named hereinafter as: Basic Issues and Advanced Issues, as it is shown in Figure 1. In particular, the former issues do not specifically involve technological aspects and they are mainly raised by differences and divergences among Member States of the European Union (EU), whereas the latter lay strongly their foundations on the IT technology growth. In the following sub-sections both these categories are presented.
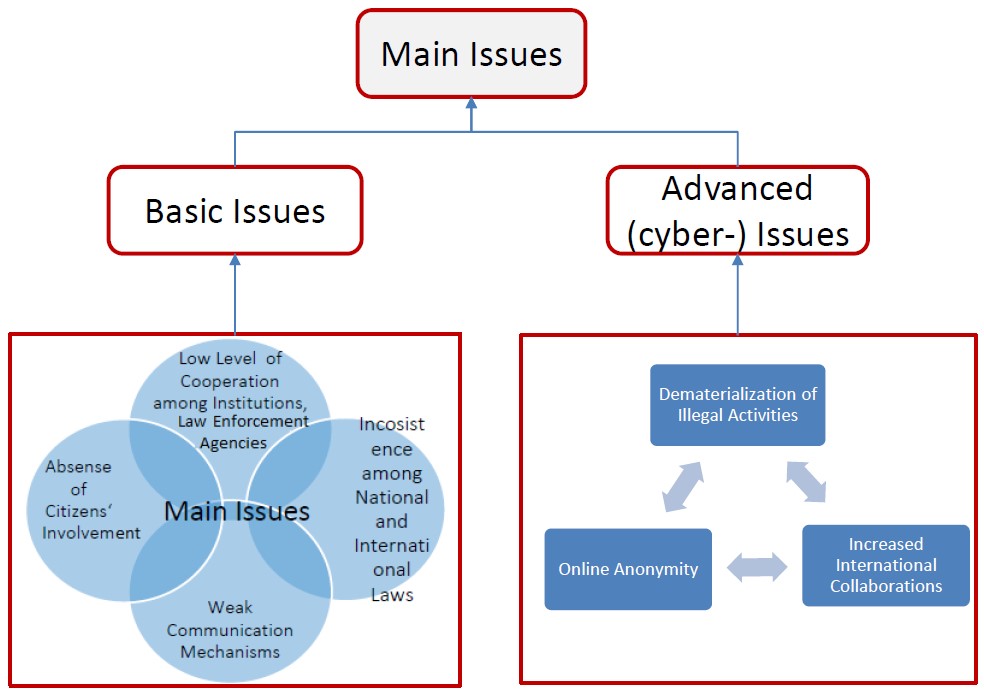
Fig. 1. A classification of the Main Issues in the EU context
In the following subsection a few details about both the categories are provided.
Basic Issues
It is widely accepted that dealing with OC and TN requires help and cooperation among states, companies and the inner state system in the global regulation of the internet. Unfortunately, the theory sometimes differs from practice, because of cultural, ethical, religious, and historical reasons that make their convergence difficult to be reached. This is the typical European scenario based on a community built around states with different background. Indeed, many gaps exist due to the differences and divergences among the member states which, in turn, raise important issues such as: Low Level of Cooperation, Weak Communication Mechanisms, Inconsistency among National and International Laws, Absence of Citizens ‘involvement.
Low Level of Cooperation. It can be perceived at different organization levels and it exists due to the lack of cooperation and trust among police forces, law enforcement agencies, as well as among national governments. This phenomenon can be observed, since nations provide hardly data of their citizens for their analysis, which could be useful for detecting suspicious activities. Furthermore, if from one side, different efforts have been conducted, among states in terms of signed treaties, to prevent criminalities; from the other side their implementation is still weak.
Weak Communication mechanisms. This issue derives partially from the previous one. Communication and notification mechanisms represent a very important aspect to counteract illicit activities. Unfortunately, most of the authorities get to know about the crime very late and it becomes difficult to stop the malicious activity and to track the criminals. As a consequence, the improvement of communication and notification mechanisms play a relevant role to prevent the risk of attacks, as well as to reduce the effect of damage, especially in terms of loss of human lives.
Inconsistency among National and International Laws. The lack of a uniform and coherent legislative system among member states is the cause of many faults, which often allow criminals to pursue their goals without too much troubles. There are multiple legislative frameworks but no single organization has the authority over all. Indeed, there are cases in which some activities are considered legal in some countries and illegal in others, thus leading to conflict at a legal level, allowing criminals to commit crimes by exploiting legal gaps.
Absence of Citizens’ Involvement. If on the one hand, the person’s damage is the primary target of criminal activities, then the people represents the most important and powerful weapon to fight criminality. Unfortunately, their involvement is still weakly considered. Specific programs devoted to citizens, which aim to create greater awareness among people and that enable them to support the authorities in the fight against crime, are not really taken into account yet.
The aforementioned issues represent the main vulnerabilities, which have been currently identified, in the EU context. Starting from them and by exploiting more sophisticated tools, new issues and illegal activities have emerged, as it is discussed in the next sub-section.
Advanced (cyber-) Issues
As mentioned before, some fundamental gaps exist among Member States. Based on such inconsistencies, further problems emerge, especially favored by the use of computer tools. Indeed, the main enabling factors, related to the IT growth, rely in:
- Dematerialization of Illegal Activities: thanks to the exploitation of the Internet, it is no more necessary to be physically in a specific place to commit a crime, to threaten a person, to steal money, or to sell drugs or weapons;
- Increased International Collaborations: it is easier to get in touch with other people, establish new contacts and relationships, as well as to organize illegal activities and improve collaborations with foreign criminal organizations;
- Online Anonymity: it is in highly exploited by criminal groups which put them outside the capacity of law enforcement and intelligence organizations. In fact, criminals are able to hide their identities by using specific techniques to coordinate activities across borders (e.g. to send encrypted messages) which allows them not to expose themselves.
Based on such factors, even well-known issues become difficult to solve with well-established solutions due to such technological factors, for example the identification represents a primary problem. For instance, well-known illegal activities (such as drug sales) are evolving, and becoming complicated to be localized in the virtual space. This is due to a lack of technological tools, innovative methods, as well as adequate resources and skilled staff. A typical example is represented by a Cold Boot attack, that is used by authorities to get the key of encrypted hard disks. Usually criminals use Tor Browser to hide their identity and specific method of full disk encryption. In order to catch a hacker and to obtain some proofs against him, a specific kind of process, called Cold Boot attack, can be followed. Unfortunately, only few countries or agencies have in-house professionals with these kind of expertise who are able to conduct such analysis.
Among the wide set of emerging illegal activities, or those that are digitally evolving thanks to the exploitation of the IT growth, the most popular are for example: Steganography, a communication technique used for hiding secret messages inside other messages or pictures; Money laundering and Black Market, an electronic payment mechanism used by criminals and terrorist organizations to remain undetected; Tumbler algorithms, it is used to transfer money from one place to another by exploiting bots, which in turn, attempt to break links between transactions and send money by dummy transactions series. Furthermore, the Dark-net, which is conceived as a network of hosts/computers not indexed by search engines where the participants interact anonymously, it is exploited by the crime organization or terrorist network to perform illegal peer to peer sharing. Botnets, a cyber-criminal tool which is created with malicious software known as malware. It transforms a computer into a bot and allows performing automated tasks on the Internet without being controlled by the rightful user.
These and many other problems are nowadays enabled from the IT growth: those make criminals free to act, by exploiting the current authority’s limitations, especially in terms of IT-skills, and those that make them unprepared to deal with Organized Crime and Terrorist Networks in the cyber space.
Note: This article is based on the following publication: A. Tundis, F. Huber, B. Jäger, J. Daubert, E. Vasilomanolakis and M. Mühlhäuser. Challenges and Available Solutions against Organized Cyber-Crime and Terrorist Networks. To appear in the 7th International Conference on Safety and Security Engineering (SAFE 2017), Rome (Italy), 6 – 8 September, 2017. doi:10.2495/SAFE170391
Author
Andrea Tundis, Technische Universität Darmstadt
Links
https://www.witpress.com/elibrary/wit-transactions-on-the-built-environment/174/36535
